
A Case Study for TrustCall 11
United States Government representatives discussed U.S. military plans earlier this month in a Signal group chat. They also inadvertently included a high-profile journalist in the chat. They would have been well-advised to use TrustCall 11 instead.
False sense of security
The Government representatives may have been lulled into a false sense of security since open source consumer apps like Signal use end-to-end encryption. While it's true that a bad actor would have difficulty decrypting the messages, the message metadata- message volume, message recipients, message date/time- is more easily hackable from the apps' web-based public notification services.
Just because the body of a message is encrypted, it doesn't mean the communications are safe.
The joy of free consumer apps
Signal's and WhatsApp's ease-of-use is undeniable. Apps like Signal and WhatsApp aim to make group chats frictionless. These apps are perfect for jawing with a large group about one's Final Four brackets or plans for a Saturday night rager.
Adding contacts to a group is intentionally seamless. If someone's inadvertently added to a group where they don't belong, it's usually no big deal. Someone may learn of a party to which they're not invited, or a non-fan may be brought into a discussion about a football game. I was recently added to a group of friends and family discussing an upcoming hair salon visit - and I'm bald.
Mistakes in free app group conversations may result in hurt feelings, boredom, or comedy. But the easy remedy is to remove oneself.
The inside threat
From a security perspective, the threat from within is often a well-meaning employee who inadvertently gives up important information. Since humans are fallible, preventing them from accidentally causing security problems is best.
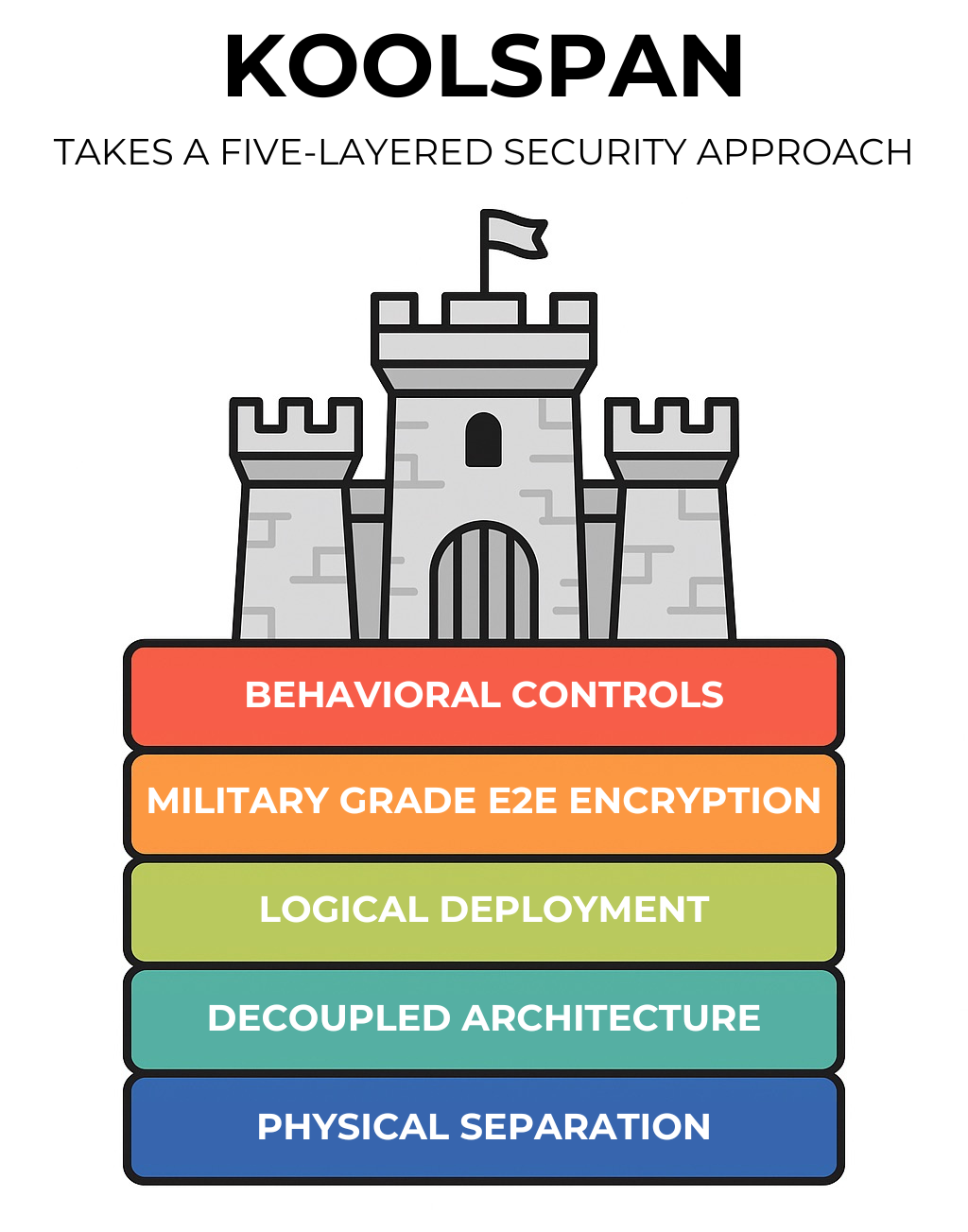
KoolSpan's security philosophy
KoolSpan takes a five-layered security approach, believing that security is as much about hardened systems as controlling user behavior, providing only the access required to perform one's job. From the basis to the top:
- The basis is physical layer. KoolSpan's TrustCall 11 product is designed to run entirely disconnected from the public web. TrustCall has its own notification services, messaging services, and administrative control of its back end.
- A decoupled architecture sits above the base encryption, where each piece communicates through APIs. The code is rigorously tested to avoid cyberattacks like SQL injection.
- The logical layer provides deployment options into standalone environments. Some users may want to deploy into a public environment, but most of KoolSpan's security-conscious customers prefer either a private cloud or on-premise deployment.
- Military-grade end-to-end encryption. But encryption is the table stakes for all communications systems.
- A behavioral layer provides administrative controls on how users may communicate within KoolSpan's products and with whom. Users may not import their public address books and create ad hoc groups of their friends. Users may create working groups but may only include their authorized colleagues
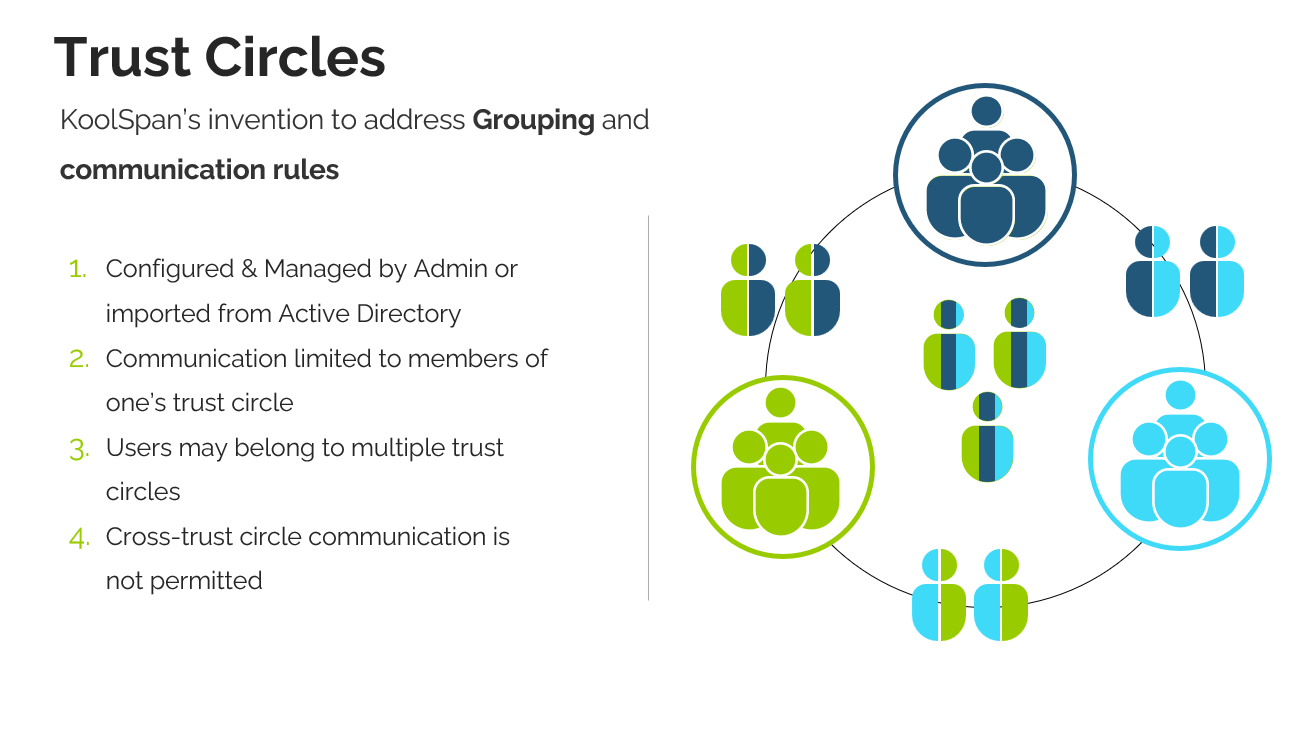
Controlling communications with Trust Circles
KoolSpan invented Trust Circles so administrators could flexibly enforce group and user rules. Users may be imported into TrustCall's back end via LDAP or CSV import. Administrators create Trust Circles - groups of users who have reason to communicate. Users may belong to multiple Trust Circles, but a communication group may include only users in the same Trust Circle. Only authorized users would have access to a sensitive chat
TrustCall 11 plays both sides
If TrustCall 11 sounds too restrictive for a free-wheeling public discussion about the Emmy Awards, it is! This isn't TrustCall's purpose. However, TrustCall 11 creatively threads the needle, providing a world-class user experience, taking design cues from WhatsApp and Signal. At the same time, TrustCall 11 keeps its users safe from their error-prone human-ness.
TrustCall 11 - The communications platform for when security and privacy are crucial.